Botnets: Covert Networks and Countermeasures

Botnets are responsible for many large-scale cyber attacks. That includes Distributed Denial of Service (DDoS) attacks and spam/phishing campaigns. They’re also behind credential-stuffing attacks that then lead to data breaches. In order to implement effective cybersecurity countermeasures against these threats, it’s important to understand what they are. So what are botnets? In a nutshell, they’re clandestine networks of compromised computers. We’ll elaborate on that and other related details in this comprehensive guide.
In the following sections, we’ll explain what botnets are, the different types that are out there, and the kinds of cyber attacks that are launched off of them. We’ll also talk about current government and private sector-initiated efforts against these malicious networks. More importantly, we’ll discuss countermeasures you can apply against these highly covert networks. We’ve got a lot to discuss, so grab that proverbial cup of coffee, and let’s get started.
What are Botnets?
A botnet is a network of malware-infected computers controlled by a centralized server. That centralized server is aptly called a command-and-control or C2 or C&C server. The infected computers are often called ‘zombies’, while the malware that infects them is called ‘botnet malware’ or simply a ‘bot’. Botnet malware can infect hundreds of even more than a million devices. Thus, the aggregate firepower of a single botnet can be enormous.
Botnet malware is designed to be stealthy so that zombie users won’t know it’s there. Some bots even employ advanced evasive techniques that make them virtually undetectable to ordinary virus scanners such as those that rely solely on signature-based detection methods. The longer the individual bots can stay hidden, the longer the botnet itself can remain operational. Bots are so stealthy, that most users whose computers have already been zombified won’t know that their devices are already taking part in, say, a DDoS attack.
In Verizon’s 2023 Data Breach Investigations Report, Denial of Service (DoS) was identified as the number one threat action variety for cyber incidents. Roughly forty percent of cyber incidents in the past year were DoS attacks. Since today’s DoS attacks require a large number of attack sources to be impactful, they’re often perpetrated by botnets and are essentially DDoS attacks. So, yes, it’s safe to say that botnets are behind a large percentage of the cyber incidents businesses experience today.

Source: 2023 Verizon Data Breach Investigations Report
Types of Botnets
There are three types of botnets: C&C, P2P, and IoT. Let’s discuss these three one by one.
Command and Control Botnets
A Command and Control or C&C botnet is a traditional botnet. As its name suggests, it’s controlled by a centralized server. That server (or servers) is in turn controlled by a human botnet operator. As soon as the botnet malware zombifies a device, the zombie establishes communications with its C&C. The C&C then issues commands to the zombie. For instance, the C&C can tell its zombies to launch a DoS attack on a target network.
Because of the C&C botnet’s centralized nature, botnet operators can easily issue commands to all of their bots. They just issue the command through the C&C, and the C&C forwards that command to all member bots. This structure, however, has one major weakness. The C&C becomes a single point of failure. If authorities manage to capture the C&C, the entire botnet will fall.
Some of the
most notorious C2-type botnets in history include the following:
Botnet | Lifespan | >Size (N of zombies) | Attack usually associated with it |
May 2009-Dec 2009 | DDoS attack | ||
Dec 2008-Nov 2016
| Hundreds of thousands
| ||
Aug 2016-Still operational
| Hundreds of thousands
| DDoS attack |
Peer-to-Peer (P2P) Botnets
While C2 botnets are highly centralized, P2P types are the exact opposite. They’re decentralized and devoid of a single point of control. Consequently, they also lack a single point of failure. This makes P2P types much harder to take down than their C2-type counterparts. Even if some bots are taken down, the entire botnet can still continue to operate.
This is possible because an infected device can serve as both a bot and a command center. A botnet operator can issue commands to one or a few of these bots, and those bots will propagate the commands to adjacent bots. Those adjacent bots can in turn propagate said commands to their neighboring bots, and so on and so forth.
Some of the most high-profile P2P botnets include the following:
Lifespan | Size (N of zombies) | Attack usually associated with it | |
Nov 2011-Jun 2014 | Hundreds of thousands | ||
Some time in 2016-Oct 2020 | Over a million | Malware distribution | |
Jan 2007-late 2008 | Tens of millions | Spam attack |
Internet of Things (IoT) Botnets
C&C and P2P botnets mainly differ in terms of architecture. One is centralized. The other is distributed. The third type of botnet we’re about to discuss doesn’t have a different architecture. Rather, its defining attribute is the devices that comprise the botnet. Traditional botnets, whether of the C&C or P2P type, usually consist of servers, laptops, or PCs. IoT botnets, on the other hand, consist of IoT devices.
These devices can range from IP cameras to printers, to routers, and even DVRs. That said, there are IoT botnets that use a centralized (C&C-type) architecture, and there are those that use a distributed (P2P-type) architecture. Mirai, for example, is an IoT botnet that uses the C&C architecture. Tsunami, on the other hand, uses a P2P architecture.
As IoT is a relatively new technology (at least compared to PC and server tech), most IoT device manufacturers focus on functionality and speed. They pay very little attention, if any, to security. That’s why many IoT devices are highly vulnerable and can easily be infected with different types of malware. That includes botnet malware. This can put businesses that use IoT devices at risk of becoming unwitting conduits for botnet-initiated cyber attacks.
Many businesses now deploy multiple IoT devices. IoT device adoption continues to climb, with a Business Insider report projecting that there will be 41 billion IoT devices by 2027. Since many of these IoT devices are plagued with vulnerabilities, these devices expose businesses to cyber threats like botnets.
The sheer number of IoT devices in operation coupled with the fact that some of these devices are designed to consume a lot of bandwidth (e.g. IP cameras) make IoT botnets capable of producing powerful DoS attacks. The Mirai DoS attacks on Krebs and Dyn websites back in 2016 are still among the largest DoS attacks in history.
Botnet Use Cases
We already mentioned some botnet ‘use cases’ like DoS attacks and spam attacks earlier in this article. However, we have yet to discuss in detail how botnets actually carry out these attacks. We’ll cover those in the following subsections.
Distributed Denial of Service (DDoS) Attacks
A DDoS attack is just a type of DoS attack that uses geographically dispersed attack sources as opposed to just one source. DDoS attacks are normally larger and consequently more disruptive than ordinary DoS attacks. Most modern-day DoS attacks—at least those that make it to the headlines—are DDoS attacks. The bots that make up a botnet are normally geographically dispersed. Hence botnet-initiated DoS attacks are most certainly DDoS attacks.
In a typical DDoS attack, botnet operators send out commands to their bots that make the bots flood the target system or network with an overwhelming volume of traffic. The incoming traffic forces the target to process requests that then consume the target’s computational resources. This causes the target to either reject legitimate requests or become unavailable.
Botnet-initiated DDoS attacks can be pretty massive. The Mirai Botnet attacks on DNS provider Dyn in 2016 reached a peak of 1.2 terabits per second (Tbps). In 2022, the Fodcha botnet, which specializes in DDoS attacks, is said to have gained the ability to launch 1 Tbps-level attacks. As mentioned earlier, a large portion of today’s cyber incidents are DoS attacks, so they’re happening quite frequently. To add more perspective, Microsoft mitigated at least half a million DDoS attacks against their global infrastructure in 2022.
Spam and Phishing Campaigns
Although botnets are often associated with DDoS attacks, they also perform other types of cyber attacks. For instance, botnets often carry out spam and phishing campaigns. To conduct these types of attacks botnets typically infect systems that have email software installed on them.
Once the infected systems are primed, the botnet operator then executes commands as well as provides the email content and optional attachments. Each bot enlisted into the campaign then starts sending out large volumes of spam and phishing emails. The Necurs botnet, for instance, is reported to have sent out millions of spam emails in less than a month in September 2018.
Credential Stuffing and Data Breaches
Botnets employed for credential stuffing are furnished with a list of login credentials. These credentials are often obtained from previous data breaches. Many users recycle the same usernames (often just their emails) and passwords across multiple sites. So even if the stolen credentials are for one site, credential-stuffing botnets are still able to break into other sites using those same credentials.
Data breaches caused by botnet-driven attacks can be more challenging from a defensive standpoint. Botnet attacks are much larger in scale and volume. Hence, multiple credential-stuffing attacks can be carried out by a single botnet at the same time. Also, botnets are able to distribute the attack across multiple IP addresses. This would make it difficult for defenders to determine where the attack is coming from.
In the 2022 Verizon Data Breach Investigations Report, botnets were identified to be among the four key paths leading to an organization’s estate. That same report also identified “use of stolen credentials” as the top threat action variety for data breaches.
Countermeasures Against Botnets
Botnets are no doubt a menace to businesses. They can cost businesses money, time, and reputation. For this reason, every organization must do its part in ensuring that its systems aren’t enslaved by a botnet. So what are the ways to counter them?
Network Monitoring and Intrusion Detection
Before a botnet can take advantage of your system’s or network’s resources, it must go through a series of stages first. These stages include infecting your system, establishing communications with their C&C or with peers, and issuing commands to your zombified system.
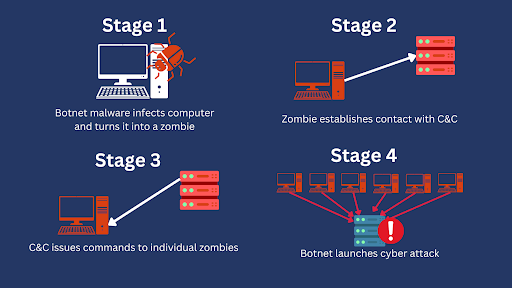
TYou can prevent a botnet from getting to the “attack” stage if you’re able to discover and act on it in those earlier stages. You can do that through proactive network monitoring. You can, for instance, employ intrusion detection systems (IDS) that monitor inbound and outbound traffic. Ideally, your IDS should be able to identify anomalous network behavior as well as connections to suspicious servers or networks. Once your IDS detects potentially malicious activity, you can conduct a more thorough investigation to uncover and, ultimately, eliminate the threat.
Education and User Awareness
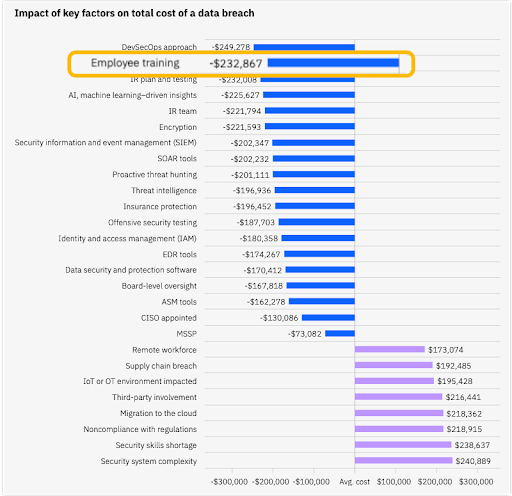
Many botnet malware infections happen due to poor end-user security practices. For instance, your system might get infected when one of your users clicks a link in a phishing email. And so, one way of minimizing botnet infections is by educating your users about cyber threats and cybersecurity. This will improve your users’ security awareness and make them more cautious when handling emails or performing any computer-related tasks. The importance of user education and awareness in improving your cybersecurity posture can’t be overemphasized. In the Cost of a Data Breach Report 2023, ‘employee training’ was identified as the second highest cost mitigator for a data breach.
You can prevent a botnet from getting to the “attack” stage if you’re able to discover and act on it in those earlier stages. You can do that through proactive network monitoring. You can, for instance, employ intrusion detection systems (IDS) that monitor inbound and outbound traffic. Ideally, your IDS should be able to identify anomalous network behavior as well as connections to suspicious servers or networks. Once your IDS detects potentially malicious activity, you can conduct a more thorough investigation to uncover and, ultimately, eliminate the threat.
>Malware Detection and Removal
The “threat” mentioned earlier was mainly the botnet malware. If you can kill the botnet malware or render it useless, you will have addressed the botnet problem. As long as the botnet malware can’t communicate with its C&C and vice versa, the botnet won’t be able to control your system. You can employ robust antivirus/anti-malware solutions to help you in that regard.
Different anti-malware solutions employ different malware detection methods. Signature-based detection used to be the de facto standard. But today, anti-malware solutions use heuristic analysis, anomaly-based detection, network traffic analysis, and other methods. No single method is perfect, so it’s best to go for a combination of solutions that allow you to employ multiple methods.
Reverse proxy solutions
Reverse proxies act as intermediaries between your host or network and external users or systems. Whenever a reverse proxy is deployed, all inbound requests to your system pass through it. As such, whoever is controlling that reverse proxy can institute rules that can allow, throttle, or completely block undesirable connections, like DDoS attacks.
Some reverse proxy service providers offer cloud-based services that are backed by multiple servers. These massive infrastructures enable them to absorb massive botnet-initiated DDoS attacks and prevent your systems from getting overwhelmed.
Collaborative Efforts and Takedowns
You are not alone in the fight against botnets. Because many botnet operators are well funded and organized—with some even backed by nation-states—cybersecurity firms are now working hand-in-hand with government law enforcement agencies to track and take these botnets down.
Here are a few examples of successful botnet takedowns and the organizations that spearheaded the takedown efforts.
Collaboration | Year of takedown | |
Trickbot | Microsoft and the Financial Services Information Sharing and Analysis Center (FS-ISAC) | 2019 |
Mariposa | Defense Intelligence, Panda Security, and Georgia Tech Information Security Center, FBI, INTERPOL | 2009 |
Conficker | Microsoft and other organizations (VeriSign, Symantec, Georgia Institute of Technology, etc), across the globe | 2008 |
Gameover Zeus | TrendMicro, Dell SecureWorks, FBI, Europol, US Department of Justice | 2014 |
Emerging Threats and Future Trends
Botnet developers and operators continue to improve the technology and tactics around botnets. Emerging threats include AI-driven botnets, which utilize sophisticated machine learning algorithms to improve their evasion tactics, enhance their propagation speed, and increase their effectiveness in launching attacks.
At the same time, cross-platform attacks are also on the rise. Botnets no longer just target traditional computers, but also smartphones, IoT devices, and even cloud platforms. These multi-pronged attacks expand the reach of botnets considerably. This makes it more challenging to defend your organization against these threats.
As these threats evolve, it becomes more crucial than ever for organizations to employ multi-layered defense strategies and stay vigilant against the ever-changing botnet landscape. Also, since cybercriminals are now incorporating AI/ML strategies into their operations, you should also start exploring ways you can leverage these powerful technologies to aid in your cybersecurity efforts.
Conclusion
Many large-scale cyber attacks like DDoS and phishing are perpetrated by botnets. Thus, in order to defend your organization against these attacks, you need to have a solid understanding of botnets. Not only must you be able to answer the question “What are botnets?”, but you must also be familiar with the different types of botnets as well as the different attacks conducted through these covert malicious networks. By understanding these key aspects, you can be more strategic in implementing countermeasures against them.
These countermeasures should include proactive defense strategies that can nip a botnet in the bud even if it employs new, highly evasive tactics. In addition, you should learn to seek assistance from cybersecurity organizations/vendors. A joint effort will make it easier to take down these massive malicious networks.
Many botnet-driven attacks can be thwarted through robust authentication systems. For example, a passwordless authentication system can render a botnet-driven credential-stuffing attack ineffective.
That’s why Kelvin Zero is building next-gen authentication and trust solutions to help organizations replace passwords and strengthen their authentication processes. With our flagship solution, Multi-Pass, organizations can easily enable enterprise-grade, phishing-resistant MFA for the full range of users, from secure passwordless logins deployed directly on employee and customer phones to military-grade passwordless MFA on offline-first smart cards. Book a demo today to learn more about Multi-Pass and how Kelvin Zero can help your organization integrate trust throughout all of its operations.