Keylogging: Surveillance and Protecting Sensitive Data

Keylogging is a form of surveillance and data theft. It’s designed to 1) spy on users when they enter login credentials and 2) steal those credentials. Once the credentials have been obtained, the keylogger, the tool used for this nefarious activity, then transmits the credentials to the threat actor’s system. This system usually comes in the form of a remote command-and-control (C2) server.

Keylogging attacks, which ultimately compromise login credentials, pose a grave danger to end users and to entire organizations. When a threat actor manages to steal a user’s login credentials, that threat actor can perform various actions on behalf of that user. For instance, if those login credentials serve as keys to a personal banking account, the threat actor can steal that victim’s funds.
Worse, if those credentials belong to a privileged account like those of a senior system administrator or a CFO, it could endanger your organization. The threat actor can perform even more business-impacting acts like setting up a backdoor to your network or syphon corporate funds.
In the 2023 Data Breach Investigations Report, “stolen credentials” is identified as the number one route attackers take to access an organization.
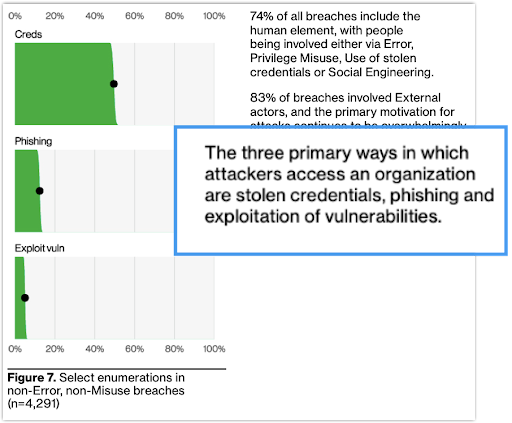
>Source: Verizon 2023 Data Breach Investigations Report
In this article, we’ll introduce you to various concepts related to keylogging. We’ll cover key attack methods, ways of detecting and preventing keyloggers, keylogging in the context of modern cybersecurity, and more.
What is Keylogging?
Keylogging per se is not a malicious activity. In its purest form, it’s just a way of recording keyboard inputs in an inconspicuous manner. Unfortunately, it’s been heavily abused by cybercriminals and, as a result, has gained a bad reputation. We’ll talk about non-malicious use cases of keylogging later in this article, but the majority of our discussions will revolve around the dark side of this covert activity. Keyloggers can be grouped into two categories—those that are built in software form and those that are built in hardware form. Of the two categories, software-type keyloggers are more common as they’re easier to build and deploy. We don’t have the exact statistics comparing the prevalence of the two categories, but if you search for ‘keyloggers’, you’ll mostly encounter articles about software keyloggers. In this article, we’ll be focusing more on software-type keyloggers. Threat actors who spread keyloggers have one immediate goal. And that is to steal login credentials. Who they target usually depends on what they want to achieve and the level of difficulty they’re willing to face. If their motivation is financial gain but prefer a lower level of difficulty, they’ll target end users. On the other hand, if their motivation is to have greater financial gain (like millions of dollars vs just a few hundred bucks), access to a large database of personal data, or access to a mission-critical server, then they’ll target privileged user accounts. The level of difficulty will likely be higher, but the ROI will be worth the extra effort.
Keylogging Attack Methods
Threat actors carry out keylogging attacks in a variety of ways. They can inject the keylogger into memory, infect a browser, employ form-grabbing, and so on. In this section, we’re going to discuss three commonly used attack methods. An understanding of how keylogging operators carry out attacks can help you gain insights for building the right defenses against these threats.
Memory-injecting keyloggers
This method involves injecting malicious code into active legitimate processes through techniques like inline hooking, DLL injection, and process hollowing. Once they’re in memory, memory-injecting keyloggers start recording keystrokes. Since these types of keyloggers only reside in memory and are essentially fileless, they can evade traditional antivirus tools that scan your filesystem for malicious files.
Man-in-the-browser keyloggers
Man-in-the-browser (MitB) keyloggers are malicious browser extensions that steal login credentials. They’re able to infect your browser when you unintentionally download a trojan after clicking a link in a phishing email or a compromised website. MitB keyloggers only affect web browsers. However, considering that most of our activities are carried out online, MitBs pose a serious threat.
Form-grabbing keyloggers
This keylogging technique grabs user credentials after they have already been entered into web forms but before they are sent to the web server. Because form-grabbing doesn’t rely on keystrokes, it’s immune to keylogger mitigation solutions like password manager auto-fills and virtual keyboards. See our discussion about these solutions later in the article for context.
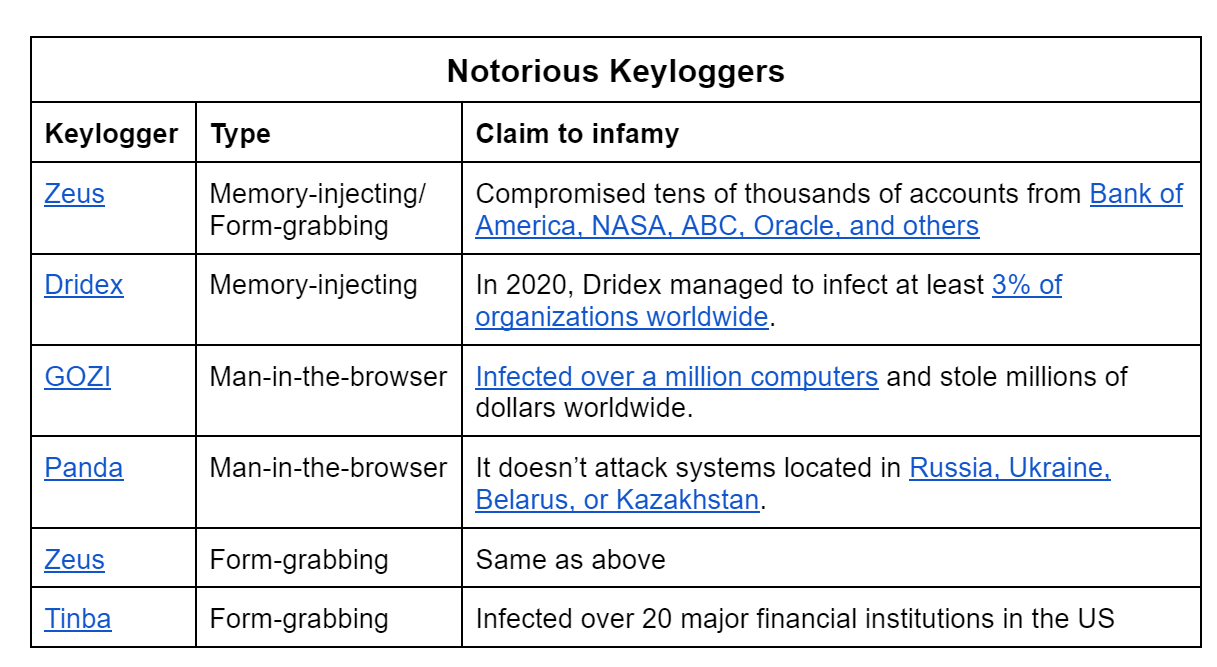
Some sophisticated types of malware employ multiple techniques for keylogging. For instance, Zeus (see table below) employs memory-injecting and form-grabbing techniques.
Detecting and Preventing Keylogging Attacks
Once a keylogger has already exfiltrated data to a threat actor-controlled network or host, your systems and user accounts will be immediately at risk of unauthorized access. Thus, it’s imperative that you institute measures to detect or, better yet, prevent keylogging attacks. Here are some tips that can help you in that regard.
Measures for detecting and/or mitigating keylogging attacks
Antivirus or anti-malware software – Software-based keyloggers are still considered malware. Hence, they can be detected and removed by capable antivirus/anti-malware tools. While the techniques used by some keyloggers—e.g. memory injection—can evade traditional signature-based antivirus tools, more advanced detection techniques like behavioral analysis can be effective against these threats.
Advanced Firewalls and Intrusion Detection and Prevention Systems (IDPS) – Most keyloggers, even memory-injection types, have to make outbound connections in order to exfiltrate stolen data. These actions can be detected by advanced firewalls and IDPSes that monitor outbound traffic. Of course, these security solutions can only be effective if they can identify connections to malicious networks or hosts. Once a malicious connection is detected, these solutions can block it, thereby preventing the keylogger from sending out stolen data.
Password managers – Password managers usually have auto-fill capabilities that eliminate the need to manually enter usernames and passwords into login interfaces. This prevents keyloggers from capturing anything during login, as no keystrokes are involved.
Virtual keyboards – Virtual keyboards are software-based tools that mimic physical keyboards. You usually interact with them through touchscreen taps or mouse clicks. Since those taps and clicks aren’t keystrokes, basic keyloggers won’t be able to record those actions. They aren’t immune to advanced keyloggers that capture screenshots or video recordings though.
Two-factor authentication (2FA) – While 2FA won’t stop a keylogging attack, it can stop unauthorized access. 2FA will make it hard for a threat actor to make use of stolen credentials that were obtained from a keylogging attack.
Measures for preventing keylogging attacks
As they say, prevention is better than cure. Here are some measures for preventing keylogging attacks.
Patching – Threat actors sometimes exploit vulnerabilities in your applications or operating systems to install keylogging malware. So, one way to prevent this kind of malware infection is by regularly patching software.
Security awareness training/education – Keylogging malware, and just about any type of malware for that matter, are usually able to infect systems through poor end-user security practices. You can prevent malware infections by teaching end users about the dangers of clicking malicious links and how to identify, say, a potentially malicious email attachment.
Keylogging Use Cases
As mentioned earlier, keylogging by itself isn’t a malicious activity. In this section, we’ll go over some of the legitimate use cases for keylogging. This will give you a different perspective on the matter. While these use cases may seem too intrusive to a person’s privacy, they’re completely acceptable to other people.
Employee monitoring and productivity assessment
Employee monitoring and productivity assessment tools like Teramind and Veriato come with keylogging capabilities that record end-user keystrokes. These tools are usually installed on company-owned devices and are used to assess employee productivity and generate relevant user analytics data.
Parental control and safeguarding children online
Keylogger-equipped parental control tools like Aispyer and SentryPC enable parents to know what their kids are typing into their devices. They’ll know, for instance, if their kids are visiting an adult site, communicating with a stranger, or involved in cyberbullying.
Law enforcement and forensic investigations
Keyloggers have also been used for law enforcement and forensic investigation purposes. In 1999, the FBI deployed a hidden keylogger to capture a decryption password belonging to Nicodemo Scarfo, a notorious mobster at that time. And then in 2007, the FBI deployed a similar software to catch an elusive bomb threat perpetrator.
Recent Examples of Keylogging Attacks
Even in recent years, keylogging hasn’t ceased to grab the headlines for malicious activities. The following examples highlight the importance of taking a more active effort in mitigating this ongoing threat.
Earlier this year, 750 victims in Singapore lost a total of $10M to a scam that duped them into installing a malicious Android app. That app used a keylogging function to steal login credentials to the victim’s online banking accounts.
Last September 4, a highly evasive malware with keylogging functionality was released in underground forums. Known as BunnyLoader, the fileless malware is designed to evade antivirus sandboxing tactics and operate from the victim device’s memory.
Keylogging in the Context of Modern Cybersecurity
Keylogging is employed in different kinds of cyber-attacks driven by different objectives. Some threat actors employ keylogging for data theft and espionage. Others use it to carry out financial fraud or identity theft. Others still use keylogging to deliver malware.
Although keylogging can be carried out as a single operation with a simple objective, it’s often incorporated in multi-staged cyber attacks. Advanced Persistent Threats (APTs), for instance, use keylogging to gain administrative access to target servers, network devices, and other systems. The credentials that keyloggers obtain can be used by the APT to gain deeper access to a target organization’s IT infrastructure.
Keylogging operations often pave the way for other cyber attacks. For example, they’re normally carried out prior to an account takeover. That said, keylogging operations also often rely on other cyber attacks before they can come into play. For instance, since keyloggers are often delivered through trojans, a prior cyber attack such as a phishing or a drive-by download campaign is usually required to deliver that trojan.
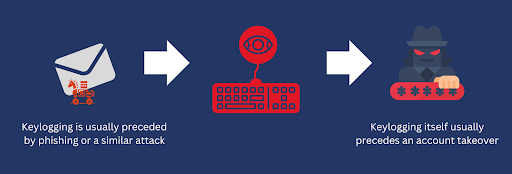
Noteworthy developments in keylogging
Just like other types of malware, keyloggers continue to evolve. Most of the developments focus on evasive techniques that aim to put keyloggers a step ahead of cybersecurity experts.
One notable development is the rise of fileless malware techniques. These techniques should force cybersecurity teams to adopt new ways of countering keyloggers. Signature-based methods, which work by inspecting file hashes, will no longer suffice.
Another development, this one perhaps even more alarming, is the infusion of artificial intelligence/machine learning (AI/ML) technologies into malicious software. Last July, cybersecurity company HYAS labs published an article about BlackMamba, a proof of concept AI-powered malware that uses ChatGPT to synthesize and resynthesize its polymorphic keylogger function.
These new developments will make it even more difficult for cybersecurity experts and vendors to detect, prevent, and act on keylogging attacks. To be effective, cybersecurity practitioners must be willing to shift to threat detection, prevention, and incident response solutions that combine more advanced methods like behavioral analysis, threat intelligence, and artificial intelligence/machine learning (AI/ML) technologies.
Conclusion
Keylogging is an ongoing threat that can compromise end users and privileged accounts and often leads to financial and data loss. To mitigate this threat, a solid understanding of its exploitation, surveillance, and data exfiltration characteristics is essential. It will help cybersecurity practitioners develop better defenses against it.
Cybersecurity experts and vendors must be willing to adopt proactive measures and use the latest technologies, including behavioral analysis, threat intelligence, and AI/ML to detect and prevent keylogging attacks. Additionally, organizations should ensure that their systems are protected from any known vulnerabilities, regularly patch security flaws, and develop strong user authentication policies. By taking these steps, organizations can reduce their risk of falling prey to a keylogging attack.
Keylogging is designed to exploit password-based authentication. Despite having been in use since the dawn of computing, it’s still the authentication method that most organizations continue to use. One way to eliminate the keylogging threat is by adopting new ways of authentication. Kelvin Zero’s Multi-Pass is built precisely for this purpose. Multi-Pass not only eliminates passwords and the risks that accompany them, but it also gets rid of time-consuming multi-step login processes. Learn more about Kelvin Zero Multi-Pass now.