Understanding SAML Authentication: A Comprehensive Overview

Most of the time, when browsing the web, we’re not communicating with one website and its services at a time but with several. Often, this happens behind the scenes to make life easier for users and for the many companies that provide services to them.
Usability is a great feature but is worth nothing without secure interactions and if unauthorized parties could easily access resources. Most security breaches stem from unauthorized access, and in 2022, the cost of a data breach reached a record high of US$4.35 million.
Providing secure authentication is a key attribute of preserving a secure interface with web applications and services. In essence, this means setting controls that ensure that only authorized individuals and systems can access the non-public data of web-based applications.
In this article, we will explore how secure authentication is achieved through an authentication standard used pervasively on the internet: SAML (Security Assertion Markup Language).
Evolution of Markup Languages
Before diving into what SAML is, let’s understand where this markup language came from and why it is widely used.
Markup languages enable information to be structured and labeled. This ensures that different computers interpret data the same way and makes it possible to customize how information is displayed. For example, HTML (Hypertext Markup Language) is all that is needed to create a simple, static webpage.
HTML is still a core component of the modern web. However, as the World Wide Web increased in size and became a vital part of most businesses, limited, static markup languages like HTML became insufficient. XML (Extensive Markup Language) was developed as a means to deliver a universal structure for defining new markup languages. At the same time, it also provides interoperability for all web server and web browser interactions. It’s like knowing a common language.
Today there are numerous markup languages based on XML that perform a range of different functions. SAML is one of the most commonly used ones and was created to address the issue of identity management and access control while ensuring interoperability.
What is SAML?
The Security Assertion Markup Language (SAML) is an XML-based standard for exchanging authorization and authentication information. In other words, it is used to confirm to web applications and services that users are who they claim they are.
When there is a need to allow a user to log in once and then gain access to various distinct web-based applications, the user’s authentication data must be shared between the systems in a standardized manner. This is the role that SAML plays. SAML eliminates the need for users to maintain multiple online identities by enabling them to authenticate once and gain access to multiple applications. This has a few different benefits, including:
- Enhanced Security: SAML increases security by eliminating additional credentials which eliminates the opportunity for identity theft. It also eliminates phishing opportunities by eliminating the number of times the user needs to login over the internet using one of those username login forms.
- Increased Access: SAML increases application access by eliminating barriers to usage, so users no longer need to type in a password, they simply click on a link and they are in the application.
- Simplified Management: SAML eliminates administration time and costs by eliminating the duplicate effort to maintain those duplicate credentials and also by eliminating all those extra help desk calls to reset those lost/forgotten passwords.
The SAML SSO (Single Sign-on) is one of the most common SAML implementations. As many users are aware of SSO, it is less known to them that SAML makes it possible.
Suppose your company, Pelican & Albatross, uses Outlook as its corporate e-mail. You want to maintain control over user access credentials, enforce password rules, and prevent terminated staff from accessing their corporate e-mail account.
This can be achieved by setting up a trusted relationship between Microsoft and Pelican & Albatross using SAML. By implementing this, whenever one of your company’s users attempts to access their work Outlook account, Microsoft would redirect their request to Pelican & Albatross’s SSO service, which would authenticate the user and relay a SAML response (approve or deny) back to the service requesting authentication, in this case, Microsoft.
The Security Assertion Markup Language— as well as other standardized languages — has been developed and maintained by OASIS (The Organization for the Advancement of Structured Information Standards). Its current version – SAML2.0 – has been in use since 2005 without losing its popularity and effectiveness.
Note: SAML is designed for web-based resource connections, unlike the LDAP standard, which addresses on-premises resources.
Key Components of SAML
There are 3 key roles (or components) in a SAML architecture:
- End User or Principal – the user who needs to access a network (web-based, Cloud) resource, such as an application, to complete their tasks.
- Service Provider (SP) – The entity that provides that application or system to users, such as Microsoft for O365, Atlassian for Jira, etc.
- Identity Provider (IdP) – The entity that intermediates the access and validates it. The IdP may use various forms of authentication, ranging from username and password to multi-factor authentication, such as biometrics.
Figure 1, shows how this flow works in practice for a typical SSO flow.
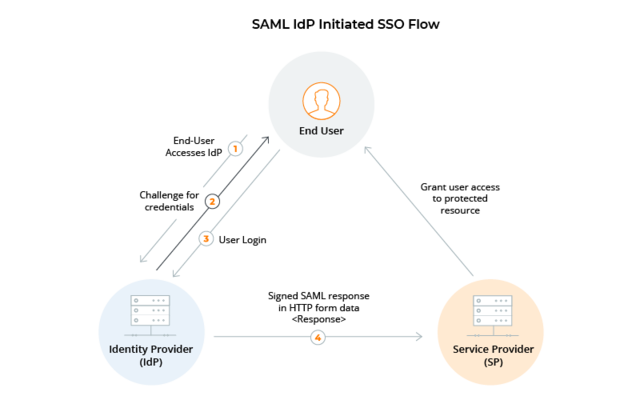
Figure 1: SAML Identity Provider-Initiated Flow
We can also use a simple analogy of a traveler passing through border control to further explain how the different relationships in a SAML flow work, wherein we would see the following scenario:
> The Principal is the traveler.
● The Service Provider is the representative of the foreign country, in this case, the border officer.
The Identity Provider is the issuer of that passport (which identifies the traveler), in this case, the home country authority.
In this example, the traveler is unable to cross the border without a valid passport. Its validity is certified by the passport issuer, who keeps digital data on the respective passport (name, validity, visas, etc.). Border control verifies this data and makes decisions based on it.
Before looking at an example of how SAML authentication works, there are a few more concepts to grasp.
>
t is worth knowing that a digital identity is more than just a user ID. A user’s digital identity is a collection of attributes, entitlements, and traits of that user. An Identity Provider manages all of this information at a central location, which is why it plays such an important role in SAML integration.
As systems have evolved into distributed environments, standards such as SAML and its protocols have enabled websites, web applications, and services to communicate effectively and securely with one another. This capability is commonly known as Interoperability.
Federation
A federated (portable) identity allows the user to be authenticated across multiple systems and companies. Federation is not possible without establishing trust in the federated environment.
Trust
For all of this to function securely, the IdP and SP need to trust one another. This ensures that the SP will accept SAML tokens generated by the IdP. An IdP will verify a user’s identity and send a token containing an attestation of their identity (as well as other attributes and claims) to the SP.
How Does SAML Authentication Work?
So far, we’ve focused on the theory, but how does it work in real life? Let’s take a simple user story.
Let’s say, Michael, working in the CRM department of a company named Happy Logistics, wants to access Salesforce through his company portal. What Michael knows is that he logs into the company network, opens the portal, clicks on the Salesforce icon, and that’s it. Even though this action is easy for him to complete, provided he has the access rights to perform it, several steps are happening “behind the scenes”. To show this we present a step-by-step breakdown of the SAML process.
In this example, Michael is considered the User/ Principal, Salesforce is the Service Provider (SP), and Kelvin0 is the Identity Provider (IdP).
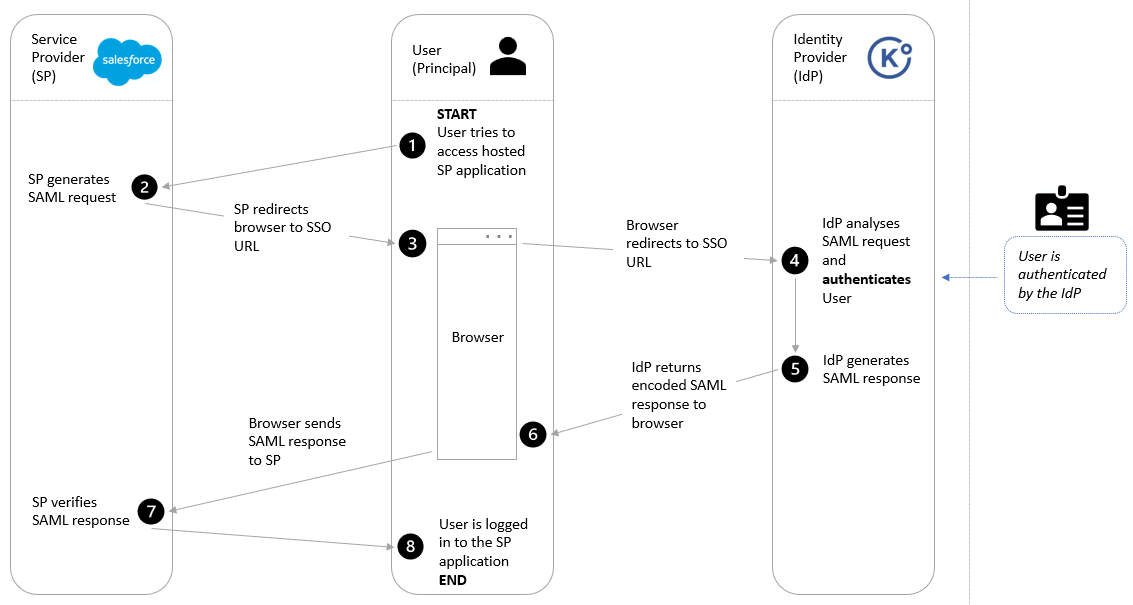
Figure 2: SAML Authentication Workflow
Step-by-step process of SAML authentication:
Step 1: The user (Principal) tries to access the hosted Service Provider application
Step 2: The Service Provider generates a SAML request
Step 3: The Service Provider redirects the Principal’s browser to the SSO URL
Step 4: The Identity Provider analyses the request and authenticates the Principal
Step 5: The Identity Provider generates a SAML response(*)
Step 6: The Identity Provider returns an encoded response to the Service Provider through the principal’s web browser
Step 7: The Service Provider verifies the response
Step 8: The user (Principal) is logged in to the Service Provider’s application.
(*) In our use case, we assume that the SAML authentication response from the IdP is positive.
Behind Michael’s easy login is a detailed SAML process, ensuring he works smoothly while the system keeps everything secure. It’s user convenience and security working hand in hand. Now Michael is happy to be able to do his job, and, hopefully, so are the customers.
SAML Assertions
We were saying earlier that the Security Assertion Markup Language is based on XML. Assertions are messages transmitted through an XML message from the IdP to the SP, containing information about the user’s identity and potentially some other attributes or authorization claims. These assertions contain statements that SPs then use to make decisions regarding the Principal’s access to the requested resource.
There are 3 SAML assertions:
- Authentication Assertion: This includes the user’s identity and information about how that identity was verified (time of sign-on, authentication methods, etc.)
- Attribution Assertion: Contains information about the user that both the IdP and SP have in their directories and can be used to match records during the authentication process.
- Authorization Assertion: Contains authorization attributes that help the SP decide if the user should be allowed to access the service.
Assertions are a key component in providing identity management and access control through SAML. The statements carried by assertions allow the SP to make the right decisions on whether to allow or deny an access request, providing companies with a crucial security safeguard and a trusted environment. However, the weight of identity administration remains with the IdP.
SAML Profiles and Protocols
SAML profiles are predefined sets of rules and guidelines that dictate how SAML messages should be exchanged between identity providers (IdPs) and service providers (SPs) in a standardized and interoperable manner.
There are many SAML profiles and protocols defined in the standard. SAML profiles define specific use cases and scenarios for implementing SAML-based authentication and authorization, ensuring consistency and compatibility between different implementations. These profiles provide a common structure for SAML messages, including authentication requests, assertions, and other related components.
The SSO profiles are prevalent — the Web Browser SSO Profile being the most common.
SAML Profiles:
- Web Browser SSO Profile (explained throughout this article) – This profile focuses on enabling SSO for web-based applications. It defines how a user can log in once on an identity provider’s system and then access multiple service providers without needing to re-enter their credentials.
- Enhanced Client or Proxy (ECP) Profile – This profile enables SSO for non-browser clients, such as desktop applications or mobile apps, using a proxy component to authenticate and authorize the user.
- IdP Discovery Profile – An SP can discover which IdP a Principal is using with the Web Browser SSO profile.
- Single Logout Profile – This profile specifies the mechanisms for logging a user out of all associated service providers when they log out from the identity provider. It ensures that the user’s session is terminated across all the connected services.
- Name Identifier Management Profile – Here, the IdP can notify the SP of changes in the format and/ or value for identifying a certain Principal.
Transmission of SAML data can take place over different protocols (specific to each profile), but a common one is SOAP. SOAP is an XML-based specification that outlines how information about web services is exchanged in a structured manner. SOAP provides a message structure and a convention of representation that is language, platform, and transport method independent.
Benefits of SAML Authentication
Let’s look at some significant advantages of using SAML authentication in web applications:
SSO – Pleased employees and administrators. The SSO capability enabled through SAML reduces the amount of time users spend authenticating. It also enables the administrator to streamline user account management and better control access rights, reducing time spent on managing accounts, permissions, and password resets.
Enhanced security – Complexity is the enemy of security. With simplified and centralized access management through SAML (assertion-based authentication, user management, and provisioning) comes increased security. Although different IDs and passwords were supposed to provide a greater level of security, they often end up being compromised due to weak and reused passwords. With SAML this is a solved problem. Authentication, which is such a core security attribute, meets its objective while enhancing the user experience (a rare combination).
Compliance – Further, with security comes the assurance that Personal Identifiable Information (PII) and any other confidential information are not disclosed to, or altered by unauthorized parties. By using SAML authentication, a company can demonstrate due diligence in implementing measures for minimizing information security risks in compliance with related regulations such as PIPEDA, CCPA, HIPAA, SOX, GDPR, and many others.
Interoperability and federation support – The Security Assertion Markup Language is one of the means for providing federation (portability) of identities and their associated entitlements, which means they can be used across business boundaries. Since federation, with the aid of SAML, allows the user to be authenticated across multiple systems and enterprises, it offers businesses and consumers a more convenient way of conducting e-commerce.
SAML Best Practices
With good cyber hygiene in place, SAML can achieve its purpose instead of becoming another attack vector. Here are some best practices for implementing the Security Assertion Markup Language authentication effectively and securely:
- Ensure proper configuration of IdPs and SPs:
Only use secure protocols and encryption standards for communication between parties (such as TLS v1.2 for transport, SHA-2 for encryption, and a trusted Certificate Authority).
Additionally, OWASP.org has crafted a list of recommendations for SAML configuration, which we found to be very useful.
- Regularly update and patch SAML implementations:
>As is the case with all of your systems, ensure that updates and patches are installed in a timely fashion, and scan your system regularly as part of a solid vulnerability management policy.
- Monitor and audit SAML transactions for potential vulnerabilities:
Ensure that logging and monitoring capabilities are in place and that alerts, incidents, or vulnerabilities are being reported and remediated.
- Provide security through the human firewall:
Since security does not only concern systems, ensure that the right employees are managing SAML and identity governance in general, that the principle of separation of duties is followed, and that regular security training is being conducted.
SAML in Real-World Use Cases
Although other standards have emerged, such as OAuth and OpenID Connect, the Security Assertion Markup Language is still prevalent and has proven to be a solid method for secure authentication. Here are some common use cases
Use Case 1 – Environments with multiple cloud-based systems and SaaS applications
Marissa’s company environment consists mainly of cloud-based services and Software-as-a-Service (SaaS) applications. She wants to integrate these into one web portal, which will allow employees to have a one-stop shop for accessing the CRM system, e-mail, HR system, Help Desk service, travel management platform, accounting system, and a few other applications.
Her employees have different user access rights to those applications and need to access them securely. Marissa also cares that her employees save time and do not worry about accessing various bookmarks, entering distinct passwords, and flooding the Help Desk with password reset requests.
To achieve these goals, Marissa implemented an authentication flow using SAML. Users could authenticate a single time with their IdP and gain access to a portal containing all their applications, eliminating the need to re-authenticate for each application
Your company may have an even more impressive amount of connectivity with other organizations and individuals. How is authentication managed securely and effectively in your business? With Kelvin Zero, not only you would be able to setup SSO with your IdP, but you would also be able to authenticate to your IdP without the need for a password with Multi-Pass.
Use Case 2 – Federation and Interoperability
An airline company can have an interaction with a user and, upon booking a plane ticket, the user may receive suggestions for accommodation, ground transport, and leisure. Often, these can be booked without prompting the user for a new account, for an extra login, or to open a different webpage. After gaining the user’s consent, their identity is federated (transferred) between the trusted companies that are part of the airline company’s web environment.
SAML provides the authentication pieces that enable federated identity management systems.
How does your company leverage secure authentication for B2B and B2C transactions in order to facilitate integration across different lines of business?
Conclusion
Takeaways
- Because most of today’s world communication is conducted through web-based processes, it is important to understand associated technologies, such as SAML authentication, and to apply them in a secure manner.
- The increased cost of managing multiple environments — along with security concerns related to entering and storing credentials on numerous services and the ongoing necessity to streamline user experiences — has driven the adoption of Single Sign-On (SSO). This technology enables users to enter their credentials just once, granting them access to a variety of applications and services through SSO.
- Flexibility, interoperability, integration, security, and compliance are interwoven benefits that can be achieved by implementing SAML.
The Future of Authentication is here Today
In an era marked by the escalating threat of data breaches and a growing imperative to safeguard our invaluable information, what could be more reassuring than fortifying your user credentials and authentication procedures with the Multi-Pass Authentication Service? With MPAS, you empower your employees with an authentication process that stores credentials offline within a biometric smart card. This means that only the individual registered with the biometric data can confidently access services, ensuring an unparalleled level of security.
Join a world where the burden of remembering and managing multiple credentials is replaced by solutions that provide enhanced security and user experience simultaneously.
If you want to discuss further how Kelvin Zero can help your business achieve this seamlessly, contact us.
Types of Authentication
Glossary
Share the page:
Join Kelvin Zero
Help us create a safer digital world for everyone
We are growing fast and are looking for like-minded and ambitious people to join our team of world-class entrepreneurs and cybersecurity experts.
Thank you!
Thank you for your submission! We will contact you shortly.
Oops..
Your message has been sent and we will contact you shortly!